Permissions' definition is explained in Social groups
. Simplifying, definition is set of permissions related to a root, for example dossier:list,new,edit,delete, whereas checking a permission would take the form dossier:new. In the definition we say the permissions related to dossier, when checking we ask whether it has one of those permissions.
Permissions can be ORed using |, for example dossier:list|@customer:on.
Permission root types
- Entities, as defined in Elephant modules.
dossier,contact,documentare examples of those entities. - Social groups, using the social group identifier prefixed with a
@, and followed with:on. - Roles, using the role name prefixed with a
#, and followed with:on. - Fuzzy roles, using the fuzzy role name prefixed with a
@, and followed with:is. - Actors, using a fixed root
@actor:, and followed with the actor name.
Fuzzy roles
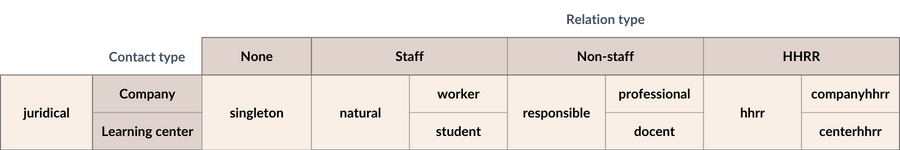
Fuzzy roles are those discovered by the application and highly dependent on interactions. Represented as @fuzzy_role:is.
| Fuzzy role | Description |
|---|---|
| su | Super user |
| admin | The user has admin capabilities |
| natural | The user has a current relation with a company or center. |
| worker | The user has a current relation with a company. |
| professional | The user has a responsible relation with a company. |
| student | The user has a non-responsible relation with a center. |
| docent | The user has a docent relation with a center. |
| responsible | The user has a responsible relation with a company or center. |
| hhrr | The user is in Human Resources. |
| companyhhrr | The user is in company's Human Resources department. |
| centerhhrr | The user is in center's Human Resources department. |
| translator | The user is a language translator. |
| listed | The user is listed in the networking directory. |
| networking | The user is in the networking. |
| premium | The user is in the premium networking. |
| singleton | The user is a freelancer or a non recognized company or center. |
| user | Comodity role for autheticated users. |
| outsider | The user comes from an Alliance member. Could only be true in Alliance servers. |
Commodity roles
Elephant includes some commodity roles, not directly related to user's role:
| Comodity role | Description |
|---|---|
| user:in | True for authenticated users. Equal to @user:is |
| lang:_lang | True if lang equals to active language |
Some examples
| Check type | Syntax | Example |
|---|---|---|
| Permissions | entity-root:permission |
dossier:list |
| Roles | #role:on |
#DossierParticipant:on |
| Social groups | @socialGroupID:on |
@customer:on |
| Fuzzy roles | @fuzzyrole:is |
@worker:is |
| Actors | @actor:actor_name |
@actor:PartnerNetwork |
Suppose a sample user assigned to Privileged Customers social group. This social group grants the DossierParticipant role, which carries dossier=list,show permissions. Therefore, dossier:show will be granted.
Scriptable permissions
This feature is in its early stages and provides a more flexible way to use the permissions starting with a @. Adds the possibility of creating complex formulas, with preferences, negations and logical operators.
| Operator | Description | Example |
|---|---|---|
| |
As in simple syntax, indicates OR. | A or B = A | B |
& |
Indicates AND. | A and B = A & B |
( and ) |
Indicate preference. | (A and B) or C = (A & B) | C |
! |
Indicates a negation. | (A and not B) or C = (A & !B) | C |